![]()
The Fortinet Security Fabric:
Cybersecurity, Everywhere You Need It

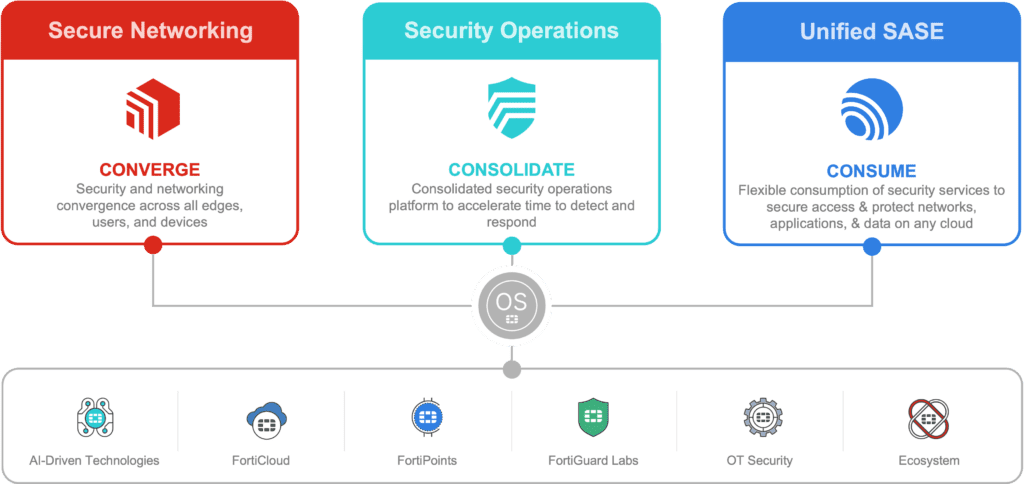
Within the Fortinet unified platform, three solutions redefine cybersecurity, helping you to respond to an ever-evolving cybersecurity landscape to meet constantly accelerating business needs.
The solution to simplifying complex networks, distributed users, and hybrid applications is the convergence and consolidation of security, all with flexible consumption models to make buying easy.
Next-Generation Firewall (NGFW)
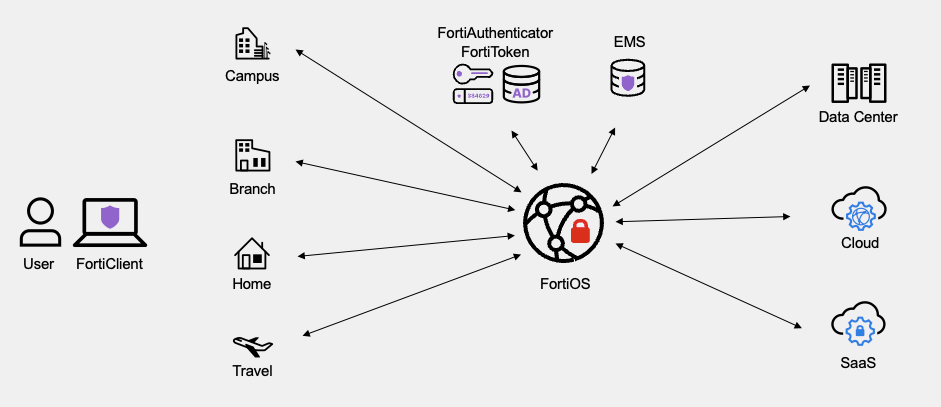
FortiGate provides flawless convergence that can scale to any location: remote office, branch, campus, data center, and cloud. We’ve always delivered on the concept of hybrid mesh firewalls with FortiManager for unified management and consistent security across complex hybrid environments. The Fortinet FortiOS operating system provides deep visibility and security across a variety of form factors.
Switching
Fortinet’s convergence of networking and security enables Ethernet to become an extension of the security infrastructure through FortiSwitch and FortiLink. Simple to deploy and manage, FortiSwitch offers many features, including NAC, without additional licensing. Our broad portfolio of secure, simple, and scalable Ethernet switches is ideal for the campus, SD-Branch, and data center.
SMB Cybersecurity Must Be Simple
With Fortinet, lean IT teams can quickly deploy however suits them, on-premises or in the cloud. Consistent security is maintained regardless of where data resides, how users connect, or how the business shifts across network, endpoint, and cloud security.
What is Zero Trust
Zero trust is a network security philosophy that states no one inside or outside the network should be trusted unless their identification has been thoroughly checked. Zero trust operates on the assumption that threats both outside and inside the network are an omnipresent factor. Zero trust also assumes that every attempt to access the network or an application is a threat. These assumptions inform the thinking of network administrators, compelling them to design stringent, trustless security measures.
Many enterprises have adopted the zero trust philosophy when designing their security architecture for several reasons:
Without zero trust architecture in place, companies unnecessarily expose themselves to costly data breaches. For example, in May 2014, hackers gained access to the addresses, names, dates of birth, and passwords of 145 million eBay users. To get in, they simply used the login credentials of three eBay employees.
If eBay had used a zero trust model equipped with at least two levels of MFA, the hackers would have needed more information than just a username and password to gain access. Requiring a USB device to be plugged into a specific computer, for example, could have saved eBay the embarrassment and loss of public trust.
Threat intelligence is a critical component of any organisation’s cybersecurity strategy. By providing real-time information on the latest cyber threats and attacks, threat intelligence tools like Fortinet and Checkpoint’s threat maps can help organisations identify and respond to threats quickly and effectively.
The FortiGuard Threat Map is an invaluable resource for organisations seeking to enhance their cybersecurity posture. It provides real-time visibility into global cyber threats, allowing proactive defence measures. As a Technical Architect, I recommend integrating this map into your security strategy.